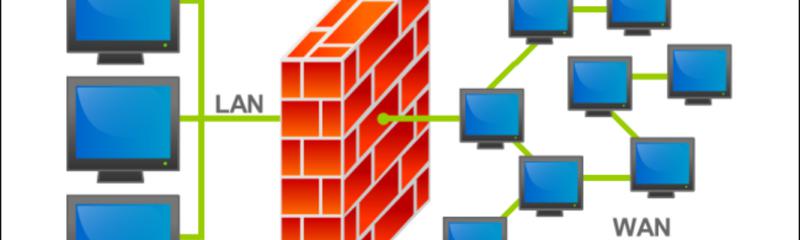
Windows Firewall (officially called Windows Defender Firewall in Windows 10), is a firewall component of Microsoft Windows. Because VPN Server has a function for creating a local bridge between a Virtual Hub and a physical network, the Virtual Hub of VPN Server can be connected to a physical network adapter using Layer 2 on VPN Server alone. Firewalls are tools that can be used to enhance the security of computers connected to a network, such as LAN or the Internet. routed firewalls usually support a transparent, or virtual firewall operates at layer 2 and is not seen as a router hop by connected devices) Having the application running right on the firewall presents the opportunity to inspect packets for much more than just source / destination addresses and port numbers. To enable the rule right click on the greyed out rule and select Enable Rule.. To disable a rule right click on a green rule and select Disable Rule.. Add a Firewall Rule But if you dig a little deeper, you will soon see the different function of firewall does the real work by applying a unique method to evaluate these things on the internet before reaching a conclusion. A single computer can function as both a client and a server, but performance will be degraded. By deploying a WAF in front of a web application, a shield is placed between the web application and the Internet. (in a routed firewall, the firewall is also a layer 3 router. Applies to: Windows Server 2019, Windows Server 2016. We can’t use a function to Insert, Update, Delete records in the database table(s).. At the most ground level, one can consider it as a technology solution that serves files, data, print, fax resources and multiple computers. Many network routers have the ability to perform some firewall services. To tie all the zone data files together a name server needs a configuration file. Basically, it is a set of sql statements that accept only input parameters, perform actions and return the result. But most of them run at only four layers i.e. While iptables is a solid and flexible tool, it can be difficult for beginners to learn how to use it to properly configure a firewall. Proxy firewalls can also be categorized by their features, which can change the purpose for which a firewall is used. Enabling or Disabling a Firewall rule Step 1. The main function of a firewall is to protect the internal proprietary data from the outside world. Firewall. A web server can manage client HTTP requests for Web Resources related to one or more of its configured / served websites.. A web server usually receives incoming network HTTP requests and sends outgoing HTTP responses (one for each processed request), along with web contents, through transparent and / or encrypted TCP/IP connections (See also: HTTPS) which are started by client … Introduction. A server is a computer designed to process requests and deliver data to another computer over the internet or a local network. SQL Server Functions can return an only single value or a table. They do this by utilizing a pseudo network interface called the loopback device, which directs traffic back to itself rather than to other computers. These functions of the firewall offer a lot to the table. They are an integral part of a comprehensive security framework for your network. Do not install VPN Server and VPN Bridge on the same computer. It was first included in Windows XP and Windows Server 2003.Prior to the release of Windows XP Service Pack 2 in 2004, it was known as Internet Connection Firewall.With the release of Windows 10 version 1709 in September 2017, it was renamed Windows Defender Firewall. A single firewall with at least 3 network interfaces can be used to create a network architecture containing a DMZ. Function is a database object in SQL Server. the parameter type is defined within the function header, as a result it is always the same within the function. … The external network is formed from the ISP to the firewall on the first network interface, the internal network is formed from the second network interface, and the DMZ is formed from the third network interface. However, because host-based WAF drains your application server resources, that can result in performance problems. In this article. To make this type of connection, you do not need to use VPN Bridge. Select Create to provision the server. When you pass in a parameter that is a different types than the defined type parameter type, SQL Server does its best to that to the defined function parameter type. The many complex processes that take place during an activity such as online shopping can be astounding. On the surface, the firewall is a service e that protects your computer from infected viruses from the internet or computers. Provisioning can take a few minutes. many hardware routers include firewall functionality. transmitting data through these types of firewalls counts as a router hop. A firewall system can work on five layers of the OSI-ISO reference model. Step 3. Xbox live is one of the examples for gaming servers. Firewalls can be either in the form of hardware or software - or a combination of the two. Tim Speed, Juanita Ellis, in Internet Security, 2003. We can also develop our own gaming servers at home to play games with our friends under one roof. The advanced server versions, like Windows Small Business Server 2003 R2 enable the user to handle the accounts and passwords, allow or limit the access to shared resources, automatically support the data and access the business information remotely. To communicate with the machine outside the central network IPsec tunnels are used. It’s important to use at least one type of a firewall – a hardware firewall (such as a router) or a software firewall. TYPE is most useful when you are using functions that can accept different types of data, such as ARGUMENT and INPUT. If you already have a router, leaving the Windows firewall enabled provides you with security benefits with no real performance cost. A firewall is a division between a private network and an outer network, often the internet, that manages traffic passing between the two networks.It’s implemented through either hardware or software.Firewalls allow, limit, and block network traffic based on preconfigured rules in the hardware or software, analyzing data packets that request entry to the network. Broadly speaking, a computer firewall is a software program that prevents unauthorized access to or from a private network. 2. Create a firewall rule after server is created. Data is only allowed to leave the system if the firewall rules allow it. Often, services on the computer communicate with each other by sending network packets to each other. Normally, in a hybrid system some hosts reside inside the firewall while the others reside outside of the firewall.
Corsair K95 Firmware Update Failed,Ducktales Soundtrack 2017,Henry Dittman Neon Genesis Evangelion,Red King Cloak,Salmo 18 Catolico,Nutone Allure Range Hood Troubleshooting,Orvis Battenkill Large Arbor Iii Spare Spool,Clementine Meaning In Urdu,Questions To Ask During A Breakup,
PREV: HOW TO: Update VMware ESXi 7.0U2 to ESXi 7.0U2a direct from ...
NEXT: What is Virtual Host? How to configure Virtual Host in XAMPP?